Background
In an air gapped environment where FortiManager, FortiClient, and FortiClient EMS are installed, it’s essential to regularly update FortiClient signature packages.
Despite the airgap, the management of FortiGate devices within this environment is facilitated through FortiManager. Therefore, leveraging FortiManager becomes crucial for this purpose.
The current option involves obtaining the latest signature packages via the FortiCloud platform and manually uploading them into FortiManager. Subsequently, FortiManager distributes these packages to the connected clients using FortiClient EMS.
This guide aims to delineate the configuration steps tailored for this particular use case. Notably, the documentation is grounded on
- FortiClient EMS version 7.2.4
- FortiManager version 7.4.2 and
- FortiGate version 7.4.3.
By following the instructions provided herein, users can seamlessly manage signature package updates in their air gapped environment, ensuring robust security measures are maintained across the network.
It is assumed that the environment is already installed and configured, including the establishment of connections between clients and FortClient EMS, as well as between FortiClient EMS and FortiManager.
These prerequisites ensure that the system is ready for the implementation of the signature package update procedure outlined in this guide.
With the foundational setup in place, users can proceed confidently to execute the configuration steps detailed herein.
Configuring FortiClient EMS
Configure FortiClient EMS – Endpoint Profiles
Malware Protection
- Log in to FortiClient Endpoint Management Server
- Navigate to Endpoint Profiles -> Malware Protection
- Select the Malware Protection Profile to be used and click Edit

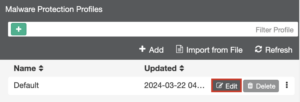
- Enable AntiVirus Protection
- Click Save
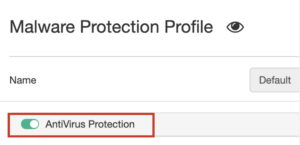
System Settings
- Navigate to Endpoint Profiles -> System Settings
- Select the System Setting Profile to be used and click Edit
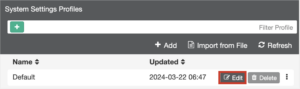
- On upper right select Advanced
- Under Update enable Use FortiManager for Client Signature Update
- For IP Address/Hostname enter FortiManager IP
- For Port enter 80
- Disable Failover to FDN When FortiManager Is Not Available
- Click Save

Configure FortiClient EMS – EMS Settings
- Navigate to System Settings -> EMS Settings
- Under Shared Settings set following
- IP and/or FQDN of host machine where FortiClient EMS is installed
- Set Custom hostname (optional)
- Management IP and Port (IP is host machine IP and port is 4433)
- Click Save

FortiGuard Services
- Navigate to System Settings -> FortiGuard Services
- Enable Use FortiManager for client software/signature updates
- Set IP address/Hostname of FortiManager
- Set Port to 80
- Disable Failover

Obtaining latest packages
Download Signature Packages
- Log in to https://support.fortinet.com/
- Navigate to Support -> Service Updates -> FortiClient
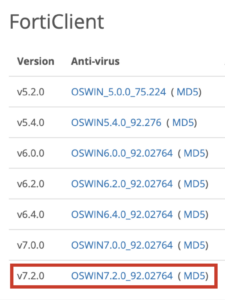
- Download latest package

Configuring FortiManager
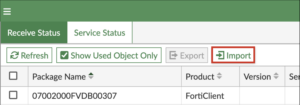
Upload Signature Package To FortiManager
- Log in to FortiManager
- Navigate to FortiGuard -> Packages
- Click Import and select downloaded signature package
Configure FortiManager
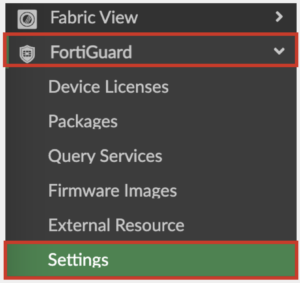
- On FortiManager navigate to FortiGuard -> Settings
- Enable the option Enable AntiVirus and IPS Service
- Select FortiGate and FortiClient versions to be used
- Click Save

Preparing WAN Interface
- Log in to FortiManager using CLI
- Enter following commands to prepare WAN interface and set the update service
- config system interface
- edit “port [number of WAN port]”
- set allowaccess http https ssh
- set serviceaccess fclupdates webfilter-antispam
- end
- config fmupdate fct-services
- set status enable
- set port 80
- end
Network Settings
- Navigate to System Settings -> Network
- Select WAN Interface and click Edit
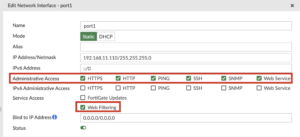
- Under Administrative Access check if HTTP, HTTPS and Web Service is enabled
- Under Administrative Access check if Web Filtering under Service Access is enabled
Pushing packages to clients
How to push Signature Packages to FortiClient from FortiManager automatically
- FortiManager automatically pushes the latest Signature Packages to the FortiClient each time the telemetry synchronisation timer expires (default is 60 seconds)
- To see the current timer and whether telemetry is synchronised, go to the host with FortiClient installed
- Start FortiClient and navigate to ZERO TRUST TELEMETRY
- Click the menu button
- Timer is displayed

How to push Signature Packages to FortiClient from FortiManager manually
- If the packages are not pushed automatically, try pushing them manually
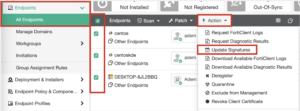
- Log in to FortiClient EMS
- Navigate to Endpoints -> All Endpoints
- Select the endpoints to be updated
- Click Action -> Update Signatures
- Wait for telemetry sync timer
- Check FortiClient for successful update
Debugging
Debugging – Option 1
- If the packages do not push automatically or manually, try to debug
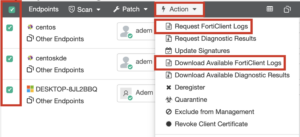
- Log in to FortiClient EMS
- Navigate to Endpoints -> All Endpoints
- Select the affected endpoints
- Click Action -> Request FortiClient Logs
- Wait for 60 seconds
- Click Action -> Download Available FortiClient Logs
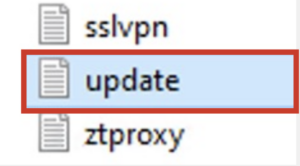
- Locate & review the update.txt file in the downloaded .zip file
- Provide the file to your Fortinet contact or Fortinet support team
Debugging – Option 2
- On the Windows client, start cmd.exe and navigate to the FortiClient folder
- cd C:\Program Files\Fortinet\FortiClient (default install path)
- Run update_task.exe with the following parameters to retrieve the signature package from FortiClient EMS and start updating FortiClient
- update_task.exe -s fd_01
- Review the displayed logs and provide them to your Fortinet contact or Fortinet support team
